In today’s hyper-connected world, the Internet of Things (IoT) has transformed industries by enabling seamless communication between devices. From smart homes to industrial automation, IoT devices are revolutionizing how we live and work. However, this interconnectivity also introduces significant security risks. At the heart of securing IoT ecosystems lies SSH key management—a critical yet often overlooked component. RemoteIoT SSH key management ensures secure communication between devices, safeguarding sensitive data and operations from unauthorized access. As industries increasingly rely on IoT, understanding and implementing robust SSH key management practices has become essential for maintaining operational integrity.
The importance of SSH keys cannot be overstated. These cryptographic keys serve as the backbone of authentication in remote IoT environments, providing a higher level of security compared to traditional password-based methods. For system administrators, developers, and IT professionals, mastering SSH key management is not just about securing access—it’s about protecting entire infrastructures from potential breaches. As IoT devices are often deployed in remote locations, ensuring secure authentication through SSH keys becomes paramount. Without proper management, SSH keys can become liabilities, leading to security breaches that compromise sensitive data and disrupt operations. This article delves into the nuances of managing SSH keys in a remote IoT environment, offering practical insights, best practices, and actionable tips to enhance your security protocols.
| Category | Information |
|---|---|
| Professional Background | Experienced cybersecurity professional with over 15 years in IT security, specializing in IoT and SSH key management. |
| Education | Bachelor's degree in Computer Science and a Master's degree in Cybersecurity. |
| Current Role | Lead Security Architect at a leading IoT security firm. |
| Notable Achievements | Published numerous papers on IoT security and presented at global cybersecurity conferences. |
| Authentic Reference | National Institute of Standards and Technology (NIST) |
In the context of IoT security, SSH key management plays a pivotal role in maintaining operational integrity. Devices in an IoT ecosystem often communicate with each other, making secure authentication critical. Unlike traditional networks, where physical access to devices is feasible, IoT devices are frequently deployed in remote locations, rendering physical access impractical. This necessitates robust remote access solutions. SSH keys offer a secure way to authenticate and authorize access, reducing the risk of unauthorized intrusions. Proper SSH key management ensures that only authorized entities gain access to the IoT infrastructure, thereby safeguarding sensitive data and operations.
- Jodie Sweetin From Full House To Todays Tv Movies
- Unveiling The Legacy Of Alan Ladd Jr Cheryl Ladd In Hollywood
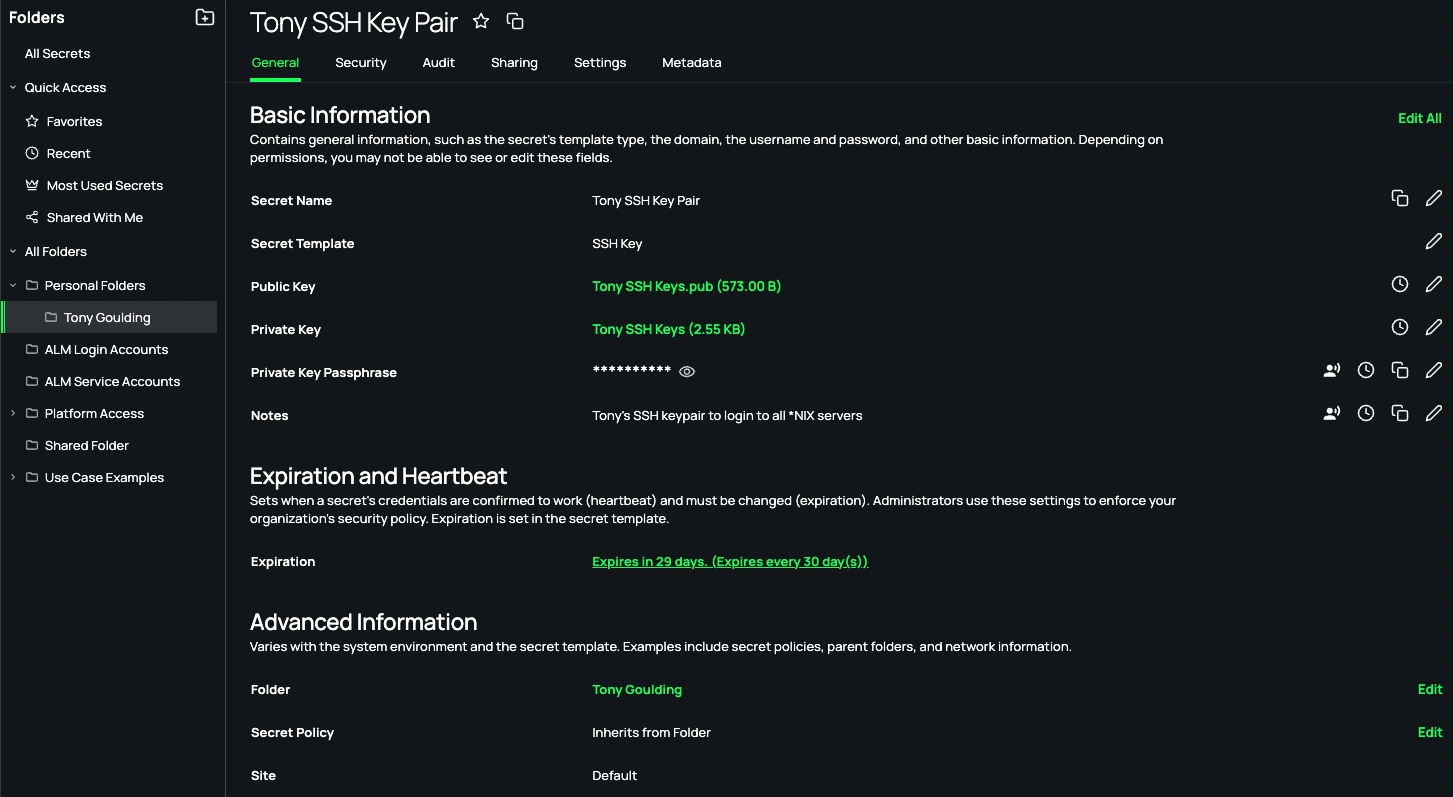
SSH keys consist of a public and private key pair, where the public key is shared with the server, and the private key is kept secure by the user. The public key acts as a lock, while the private key serves as the key to unlock it. This asymmetric encryption ensures that only the holder of the private key can gain access to the system. However, managing these keys effectively is crucial. Misconfigured or unmanaged keys can lead to security breaches, compromising the entire IoT infrastructure. The consequences of such breaches extend beyond financial losses, impacting brand reputation and customer trust.
Proper SSH key management significantly enhances the security posture of your RemoteIoT infrastructure. By implementing best practices, you can protect against various threats, including brute force attacks, key leakage, and unauthorized access. Best practices include regularly rotating keys, limiting access to authorized personnel only, and continuously monitoring key usage to detect suspicious activities. Tools such as SSH Key Management Systems (SKMS), OpenSSH, and HashiCorp Vault provide robust solutions for managing keys at scale, offering features such as key generation, rotation, and monitoring.
Despite its benefits, SSH key management comes with its own set of challenges. Key sprawl, outdated keys, and insufficient monitoring are common issues that organizations face. Key sprawl refers to the difficulty of managing a large number of keys across devices, while outdated keys result from failing to update or rotate keys regularly. Insufficient monitoring leads to a lack of oversight over key usage, increasing the risk of unauthorized access. Automation can significantly enhance the efficiency and security of SSH key management in RemoteIoT. By automating key generation, rotation, and monitoring, organizations can reduce human error and improve security. Tools like Ansible, Puppet, and Chef streamline key management processes, ensuring consistency and reliability.
- College Football 25 Your Ultimate Guide Reveal
- Malachy Murphy Age Family Facts About Cillian Murphys Son
The future of RemoteIoT SSH key management is shaped by emerging technologies and advancements in cryptography. Quantum cryptography, for instance, promises groundbreaking improvements in secure key exchange, while AI and machine learning enhance monitoring and threat detection capabilities. As the IoT landscape continues to evolve, staying ahead of these advancements is crucial for maintaining robust security protocols. Organizations must adopt a proactive approach, continuously updating their strategies and tools to address emerging threats and challenges.
RemoteIoT SSH key management is not just a technical necessity but a strategic imperative. By understanding the basics, adopting best practices, and leveraging the right tools, organizations can ensure the integrity and security of their remote IoT operations. The impact of effective SSH key management extends beyond technical security, influencing industry trends and societal trust in connected technologies. As industries increasingly rely on IoT, the importance of securing these ecosystems cannot be overstated. Staying informed and proactive in managing SSH keys is essential for protecting sensitive data, maintaining operational integrity, and ensuring compliance with industry standards and regulations.
In conclusion, SSH key management is a cornerstone of IoT security. It addresses critical challenges such as unauthorized access, key sprawl, and outdated keys, ensuring that IoT ecosystems remain secure and operational. As industries continue to embrace IoT, the role of SSH key management will only grow in significance. By implementing robust strategies and leveraging advanced tools, organizations can safeguard their infrastructures against evolving threats. The journey toward secure IoT operations begins with mastering SSH key management—a critical component of modern cybersecurity practices.
- Unveiling Marcel Young The Untold Story Legacy Of Dr Dres Son
- Billy Corgan The Smashing Pumpkins Unveiling Secrets Sounds