RemoteIoT devices have transformed the landscape of modern technology, enabling users to monitor and manage systems from any corner of the globe. In today's hyper-connected world, these devices are indispensable for industries ranging from manufacturing to healthcare. However, with great power comes great responsibility, and ensuring the security of these devices is paramount. This guide will delve into the nuances of using SSH (Secure Shell) to establish secure connections to your RemoteIoT devices, providing you with the tools and knowledge to manage your systems effectively.
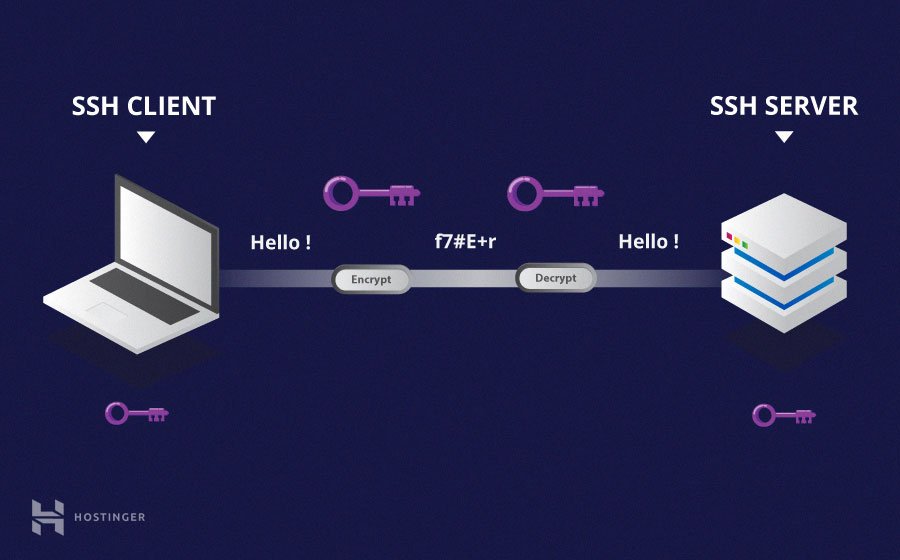
SSH has become the backbone of secure remote access, offering encryption and authentication mechanisms that safeguard against unauthorized access and data breaches. For RemoteIoT devices, SSH ensures that all communication between the user and the device remains confidential and tamper-proof. As industries increasingly adopt IoT solutions, understanding SSH and its applications is not just beneficial—it's essential. This guide will walk you through the setup process, troubleshoot common issues, and explore advanced configurations to optimize your IoT network.
| Category | Details |
|---|---|
| Technology | SSH for RemoteIoT Devices |
| Application | Industrial Automation, Smart Homes, Environmental Monitoring |
| Prerequisites | SSH Client, Stable Internet Connection, Device Credentials |
| Best Practices | Strong Passwords, Key-Based Authentication, Limited Access |
| Reference | SSH Official Website |
Before diving into the specifics, it's crucial to understand the foundational aspects of RemoteIoT devices and SSH. These devices are equipped with features such as real-time data monitoring, automated system updates, remote diagnostics, and seamless integration with cloud platforms. These capabilities make them invaluable for businesses seeking to enhance operational efficiency. However, without proper security measures, these devices can become vulnerable to cyber threats. SSH addresses these concerns by providing a secure channel for communication, encrypting all data transmitted between the user and the device.
- Inside Jenna Dewans Life Kids Family Tatum Romance
- Zach Tops Net Worth 2024 Career Earnings Success Story
SSH, or Secure Shell, is a cryptographic network protocol that facilitates secure data communication, remote command execution, and other secure network services. Its benefits include robust data encryption, reliable authentication mechanisms, protection against eavesdropping, and support for file transfer. In the context of RemoteIoT devices, SSH ensures that your connection remains secure, safeguarding against unauthorized access and potential data breaches. This guide will equip you with the skills needed to establish and maintain secure connections, empowering you to manage your IoT devices with confidence.
Before proceeding with the setup, ensure you have the necessary prerequisites in place. On the hardware side, you'll need a computer or laptop with an SSH client installed, a stable internet connection, and a RemoteIoT device with SSH enabled. On the software side, you'll require an SSH client such as PuTTY for Windows or OpenSSH for Linux/Mac, along with access credentials for the RemoteIoT device. Having these prerequisites ready will streamline the process and ensure a smooth setup experience.
Now, let's explore the step-by-step process of establishing an SSH connection to your RemoteIoT device. Begin by installing an SSH client if you haven't already. For Windows users, PuTTY is a popular choice, while Linux and Mac users can utilize the built-in OpenSSH client. Next, gather the IP address and login credentials for your RemoteIoT device, which are typically provided in the device documentation or can be obtained from the network administrator. Once you have this information, open your SSH client, enter the device's IP address, and authenticate using the provided credentials to establish a secure connection. Finally, verify the connection by accessing the device's command-line interface, ensuring that the connection is stable and functional.
- Malachy Murphy Age Family Facts About Cillian Murphys Son
- October 24th Zodiac Traits Compatibility More Discover Now
While setting up an SSH connection, you may encounter some common issues. For instance, if you receive a "Connection Refused" error, ensure that the RemoteIoT device's SSH service is running and that the firewall allows incoming connections on port 22. If you experience authentication failure, double-check your login credentials and ensure that the SSH keys are correctly configured if using key-based authentication. Network connectivity issues can also arise, so verify that your internet connection is stable and that the device's IP address is accurate. Addressing these issues promptly will help you establish a secure and reliable connection.
Security is paramount when dealing with remote access to IoT devices. To enhance the security of your SSH connections, adopt the following best practices. First, use strong passwords that are unique and difficult to guess, avoiding default credentials at all costs. Second, enable key-based authentication, which provides an additional layer of security by eliminating the need for passwords. Third, limit SSH access to trusted IP addresses and disable root login to minimize the risk of unauthorized access. Implementing these measures will significantly bolster the security of your IoT network.
Once you've mastered the basics, consider exploring advanced configurations to optimize your RemoteIoT device's performance and security. One such configuration is port forwarding, which allows external access to your device securely. Another is SSH tunneling, which enables you to access services running on the device, such as databases or web servers, without exposing them directly to the internet. Additionally, configuring automated backups ensures that your device's data is regularly saved and can be restored in case of failure. These advanced configurations can elevate your IoT setup, enhancing both functionality and security.
Several tools and software can enhance your experience when working with RemoteIoT devices over SSH. Popular SSH clients include PuTTY for Windows and OpenSSH for Linux/Mac. Monitoring tools like Netdata and Prometheus provide valuable insights into your device's performance, helping you identify potential issues before they escalate. By leveraging these tools, you can gain a deeper understanding of your IoT network and make informed decisions to improve its efficiency and reliability.
SSH's versatility makes it applicable to various use cases in the context of RemoteIoT devices. In industrial automation, SSH enables you to monitor and control equipment remotely, ensuring optimal performance and reducing downtime. For smart home systems, SSH allows you to access and manage devices such as thermostats and security systems from anywhere in the world. In environmental monitoring, SSH facilitates the collection and analysis of data from sensors deployed in remote locations, providing valuable insights for research and decision-making. These use cases highlight the broad applicability of SSH in IoT applications, underscoring its importance in modern technology.
Looking to the future, emerging trends in IoT and SSH promise to further enhance the security and performance of remote connections. Quantum-resistant encryption aims to develop methods that can withstand quantum computing attacks, ensuring long-term security for IoT devices. AI-driven security utilizes artificial intelligence to detect and respond to security threats in real time, enhancing the protection of IoT networks. Additionally, 5G connectivity offers increased bandwidth and reduced latency, improving the performance and reliability of remote IoT connections. As technology continues to evolve, the role of SSH in securing IoT devices will only grow more critical.
In conclusion, this guide has provided a comprehensive understanding of how to establish secure connections to your RemoteIoT devices using SSH. By following the steps outlined and implementing the recommended best practices, you can ensure the security and efficiency of your IoT network. As industries increasingly adopt IoT solutions, mastering SSH is not just a skill—it's a necessity. We invite you to share your thoughts and experiences in the comments section below and explore other articles on our site for more insights into IoT and related technologies. Together, let's build a safer and more connected future.
- Unveiling Marcel Young The Untold Story Legacy Of Dr Dres Son
- Kannada Movies 2025 Stay Safe Informed About Movierulz Alternatives