Connecting to remote IoT devices using SSH is an indispensable skill for developers and IT professionals in today's hyper-connected world. As the Internet of Things continues to expand, the need for robust security measures to protect sensitive data and maintain system integrity becomes increasingly critical. IoT devices are now ubiquitous, from smart homes to industrial automation, and securing their communication channels is no longer optional but essential.
The rapid proliferation of IoT devices has placed managing and securing remote systems at the forefront of organizational priorities. SSH (Secure Shell) provides a secure protocol for remote access, ensuring encrypted communication between devices. This guide will walk you through the process of setting up and utilizing SSH for remote IoT devices, offering practical insights and best practices for both beginners and seasoned professionals.
| Category | Details |
|---|---|
| Name of Protocol | SSH (Secure Shell) |
| Primary Function | Facilitates secure communication between devices over unsecured networks |
| Default Port | 22 |
| Compatibility | Linux, macOS, Windows, various IoT platforms |
| Security Features | Encryption, authentication, integrity protection |
| Reference | OpenSSH Official Website |
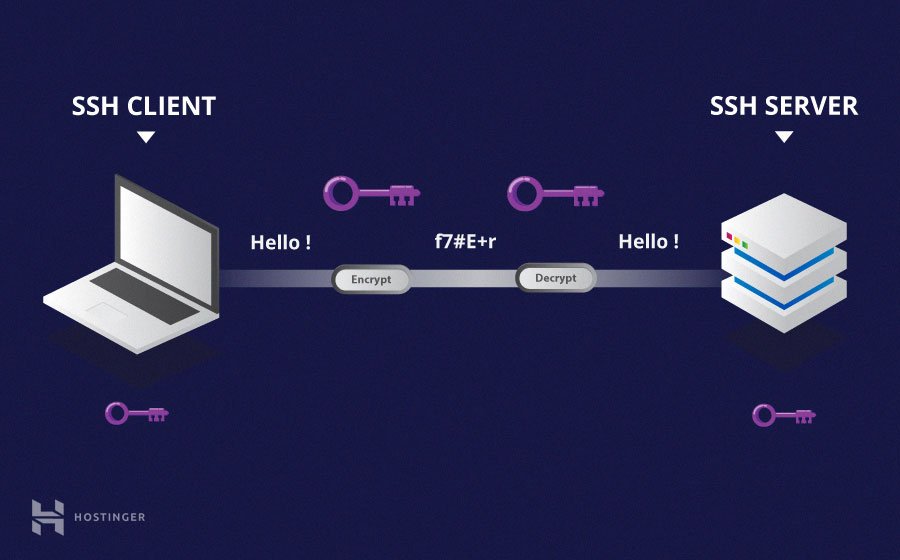
SSH, or Secure Shell, is a network protocol that ensures secure communication between devices over an unsecured network. It is widely adopted for remote access to servers, routers, and IoT devices due to its ability to encrypt data transmission. SSH operates on port 22 by default and provides a secure alternative to less secure protocols such as Telnet and FTP. Its versatility across operating systems, including Linux, macOS, and Windows, makes it a go-to solution for managing diverse applications. In the context of IoT devices, SSH plays a pivotal role in securely managing and maintaining remote systems. Whether configuring sensors, monitoring environmental conditions, or updating firmware, SSH ensures interactions with IoT devices remain protected from unauthorized access and data breaches.
- Unveiling Iowa Hawkeyes Womens Basketball Success Passion
- Crissy Henderson Ronnie Radke A Love Storys Resilience Rise
Using SSH for IoT devices offers several advantages over other communication protocols. Encryption is a cornerstone of SSH, ensuring all data transmitted between devices remains confidential and tamper-proof. Additionally, SSH supports multiple authentication methods, including password-based and public-key authentication, which guarantees only authorized users can access the device. Its compatibility with a wide range of IoT platforms and operating systems makes it easy to integrate into existing systems. Moreover, SSH connections are reliable, even in unstable network conditions, making it an ideal solution for securing IoT devices deployed in remote or untrusted locations.
Before setting up SSH for your IoT device, it is crucial to ensure you have the necessary hardware and software components. On the hardware side, you will need an IoT device with an SSH-capable operating system, such as a Raspberry Pi or an ESP32 running Linux. A stable internet connection or local network access is also essential, as is a computer or laptop with an SSH client installed, such as PuTTY for Windows or Terminal for macOS/Linux. On the software front, an SSH server must be installed on your IoT device, typically OpenSSH, along with an SSH client on your local machine. Basic knowledge of command-line operations will also be beneficial in navigating the setup process.
Setting up an SSH server on your IoT device involves a series of straightforward steps. Begin by enabling SSH on your device. For instance, on a Raspberry Pi running Raspbian, open the Raspberry Pi Configuration tool by typing `sudo raspi-config` in the terminal, navigate to "Interfacing Options," and enable SSH. Reboot your device to apply the changes. If your IoT device lacks an SSH server, you can install OpenSSH using the command `sudo apt update && sudo apt install openssh-server`. Once installed, customize the SSH server settings by editing the configuration file located at `/etc/ssh/sshd_config`. Common configurations include changing the default SSH port and disabling password authentication in favor of public-key authentication for enhanced security.
- Horror Gems Synapse Films News You Cant Miss
- Aaron Kendrick De Niro Rising Star Hollywood Legacy Unveiled
With the SSH server successfully set up on your IoT device, connecting to it remotely via an SSH client is the next step. Begin by identifying the IP address of your IoT device using the command `hostname -I` in the device's terminal. This will display the assigned IP address. On your local machine, open the SSH client and enter the command `ssh username@device_ip_address`, replacing "username" with the appropriate user account on your IoT device and "device_ip_address" with the obtained IP address. This command initiates the secure connection between your local machine and the IoT device.
While SSH inherently provides a secure communication channel, adhering to best practices further enhances security. Using strong passwords is a fundamental step in safeguarding SSH accounts. Additionally, enabling public-key authentication and disabling password-based authentication adds an extra layer of security. Changing the default SSH port to a custom port reduces the risk of automated attacks, while limiting user access to specific individuals or groups minimizes potential security risks. Implementing these practices fortifies your IoT devices against unauthorized access and potential cyber threats.
Occasionally, issues may arise when connecting to your IoT device via SSH. Common problems include connection refusal, incorrect credentials, and network issues. To resolve connection refusal, ensure the SSH server is operational and the device's firewall permits SSH traffic. Verify the username and password or public key used for authentication if credentials are incorrect. Network issues can be addressed by checking the device's network connection and confirming it has a valid IP address. If the problem persists, consulting the SSH server logs can provide more detailed information about the issue.
SSH offers advanced features that expand its functionality for IoT applications. SSH tunneling allows secure access to services running on your IoT device, such as web servers or databases. Port forwarding enables specific ports from your local machine to be forwarded to the IoT device for remote access to services. SSHFS facilitates mounting remote file systems on your local machine, streamlining file management. Exploring these features can unlock new possibilities for managing and interacting with your IoT devices.
Automation with SSH can significantly improve efficiency in managing IoT devices. Writing scripts automates routine tasks, such as updating firmware or collecting sensor data. Scheduling SSH commands to run at specific intervals through cron jobs ensures regular maintenance tasks are performed without manual intervention. Remote monitoring using SSH allows real-time tracking of device performance and health metrics, providing insights into system behavior and potential issues. Leveraging automation not only streamlines operations but also reduces the need for manual intervention in managing IoT infrastructure.
SSH's role in securing IoT devices extends beyond technical implementation. Its adoption reflects broader trends in the tech industry, where cybersecurity is increasingly prioritized. Celebrities and industry leaders alike emphasize the importance of secure communication in an era where data breaches and cyberattacks are rampant. For instance, tech giants like Apple and Google have integrated SSH-like protocols into their products to enhance user security. The impact of SSH on society is profound, as it empowers individuals and organizations to protect sensitive information while fostering innovation in interconnected technologies.
In the realm of IoT, SSH serves as a cornerstone for secure communication, aligning with global efforts to build a secure and connected future. By following the steps outlined in this guide and adhering to security best practices, you can establish a secure connection to your IoT devices and harness the full potential of SSH. Whether you are configuring sensors, monitoring environmental conditions, or updating firmware, SSH ensures your interactions with IoT devices remain protected. As the IoT landscape continues to evolve, embracing SSH's capabilities will be instrumental in navigating the challenges and opportunities of this dynamic field.
- Pink Bear Gojo Statue Mustknow Details Where To Buy
- Unveiling The Vanderbilt Legacy Wealth Mansions More