In today’s hyper-connected digital era, the secure integration of remote IoT devices into a Virtual Private Cloud (VPC) using a Raspberry Pi has become a necessity for both hobbyists and professionals. The proliferation of smart devices and the shift toward remote work have heightened the importance of safeguarding communications between IoT devices. This article walks through the detailed process of setting up a secure connection, complete with free download options and practical tips to fortify your IoT network.
For both beginners and seasoned tech enthusiasts, understanding how to configure a secure IoT environment is imperative. From selecting the right tools to implementing industry-standard practices, this guide provides actionable insights to protect your devices and data. As we delve into securely connecting remote IoT devices to a VPC using Raspberry Pi, we will also explore free download resources that simplify the process. By the end of this article, you will have a thorough understanding of the tools, techniques, and strategies required to ensure your IoT infrastructure remains secure.
| Aspect | Details | References |
|---|---|---|
| Topic Focus | IoT Security and Raspberry Pi | Raspberry Pi Official Website |
| Industry Relevance | Smart Devices, Remote Work, VPC | N/A |
| Primary Tools | Raspberry Pi, MQTT, SSL/TLS | N/A |
| Key Threats | Device Hijacking, Data Breaches | N/A |
IoT security has emerged as one of the most critical challenges in the tech landscape, with devices ranging from home automation systems to industrial sensors often lacking robust security measures. This vulnerability makes them prime targets for cyberattacks, which can compromise entire networks. A breach in a single device could lead to significant data theft, financial loss, or even physical harm, depending on the application. For instance, in healthcare, compromised IoT devices could disrupt patient monitoring systems, while in manufacturing, unauthorized access could halt production lines. Thus, securing remote IoT VPC connections is not just about protecting data but also ensuring the integrity of critical systems.
- Nikola Jokics Brothers Strahinja Nemanja Family Basketball
- Richard Geres Wife Unveiling Alejandra Silva Their Love Story
As IoT devices continue to integrate into critical infrastructures, from healthcare to manufacturing, the stakes have never been higher. A breach in one device can compromise an entire network, leading to data theft, financial loss, or even physical harm. For example, in 2016, the Mirai botnet attack demonstrated how unsecured IoT devices could be leveraged to launch large-scale Distributed Denial of Service (DDoS) attacks, crippling major websites. The attack highlighted the urgent need for robust security measures in IoT environments. By securing remote IoT VPC connections, you can protect sensitive information, prevent malicious actors from taking control of your devices, and ensure compliance with industry regulations.
A Virtual Private Cloud (VPC) provides a secure and isolated network environment for hosting and managing IoT devices. Cloud service providers like AWS, Microsoft Azure, and Google Cloud offer VPC solutions that allow you to configure your IoT devices within a private network, shielding them from external threats. The benefits of using a VPC for IoT devices include enhanced security through network isolation, flexible configuration options for device management, and scalability to accommodate growing IoT deployments. Setting up a VPC involves selecting a cloud provider, defining network parameters, configuring security groups and access control lists (ACLs), and deploying IoT devices within the VPC to test connectivity.
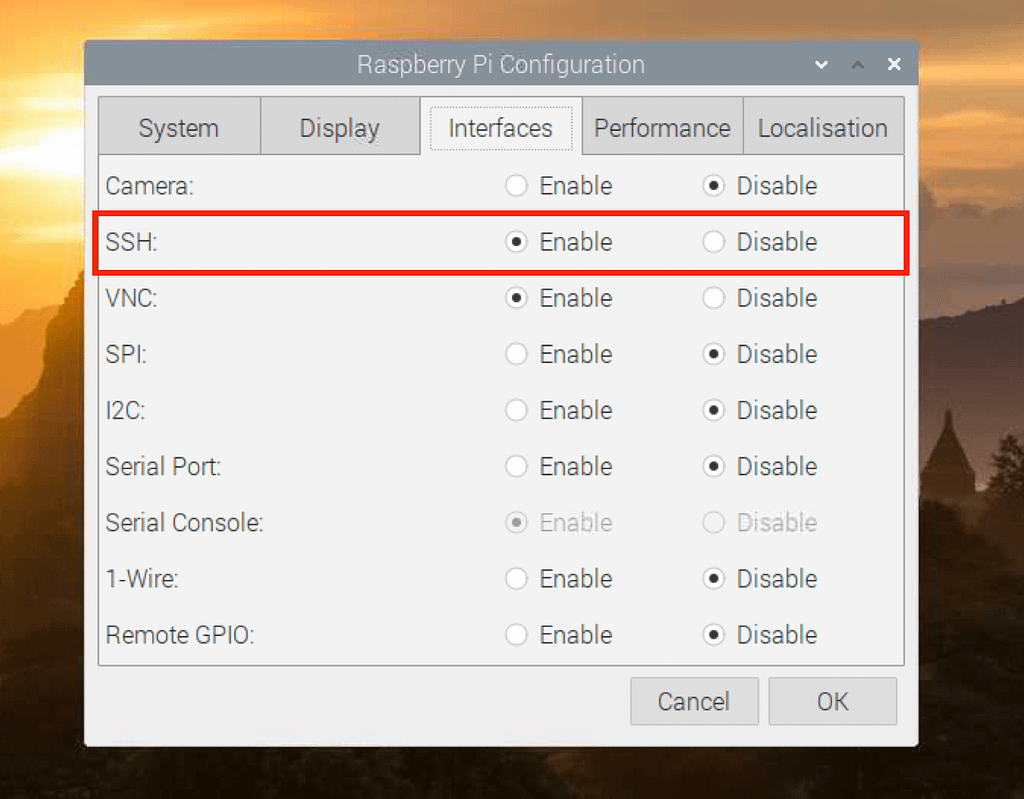
Raspberry Pi stands out as a versatile and cost-effective platform for IoT projects. Its compatibility with various operating systems and programming languages makes it ideal for establishing secure connections between IoT devices and a VPC. Configuring a Raspberry Pi for secure IoT connections involves installing an operating system like Raspbian or Ubuntu, configuring SSH for remote access, installing necessary software packages such as MQTT brokers or SSL/TLS libraries, and testing the connection between the Raspberry Pi and IoT devices. To ensure security, it is essential to change default passwords, regularly update the operating system and installed software, and implement firewalls and intrusion detection systems.
- Joshua Morrows Children Names Ages Family Life Unveiled
- Zach Tops Net Worth 2024 Career Earnings Success Story
Several free tools and resources are available to facilitate secure IoT connections. For instance, MQTT brokers like Mosquitto and HiveMQ offer free versions suitable for small-scale deployments. Encryption libraries such as OpenSSL and GnuTLS provide robust encryption capabilities, while network monitoring tools like Wireshark and Nmap help identify and mitigate potential security threats. When selecting tools for your IoT project, consider compatibility with your Raspberry Pi and IoT devices, ease of installation and configuration, and the availability of community support and documentation. To maximize the effectiveness of these tools, regularly update them to ensure they have the latest security patches, document your configurations and settings for future reference, and test them in a controlled environment before deploying them in a production setting.
Secure communication protocols are vital for protecting data transmitted between IoT devices and a VPC. Common protocols include MQTT (Message Queuing Telemetry Transport), CoAP (Constrained Application Protocol), and HTTPS. MQTT is lightweight and ideal for resource-constrained devices, while CoAP is designed for low-power and low-bandwidth networks, and HTTPS provides secure web communication using SSL/TLS encryption. Configuring MQTT for secure communication involves installing an MQTT broker on your Raspberry Pi or a cloud-based server, enabling SSL/TLS encryption, and setting up username and password authentication for authorized access. Ensuring data integrity in IoT environments requires the use of digital signatures to verify the authenticity of data, implementing checksums to detect and correct errors, and regularly auditing logs to identify and address any discrepancies.
Best practices for securing IoT VPC connections include network segmentation, regular security audits, and employee training and awareness. Segmenting your network ensures that IoT devices are isolated from other systems, reducing the risk of lateral movement in case of a breach. This can be achieved using VLANs or subnets to create distinct network zones for IoT devices. Conducting regular security audits helps identify vulnerabilities and ensures compliance with security standards. Automating audits using tools like Nessus or OpenVAS can streamline the process. Educating your team about IoT security best practices and encouraging them to report suspicious activities promptly is crucial in minimizing human error, a significant factor in security breaches.
Emerging technologies are shaping the future of IoT security, with blockchain providing decentralized and tamper-proof data storage, AI and machine learning enhancing threat detection and response capabilities, and quantum cryptography offering unparalleled encryption strength for secure communications. As IoT adoption grows, governments and organizations are developing regulations to ensure data privacy and security. Staying informed about these regulations is essential for maintaining compliance. The evolving threat landscape demands continuous adaptation, and staying updated with the latest security trends and investing in tools and training is necessary to address emerging challenges.
As the world becomes increasingly interconnected, the need for secure IoT VPC connections using Raspberry Pi grows. This involves a combination of technical expertise, strategic planning, and adherence to best practices. Following the steps outlined in this guide will protect your IoT infrastructure from potential threats and ensure seamless communication between devices. We encourage you to explore the free tools mentioned in this article to enhance your IoT security. Share your experiences and insights in the comments below, and don’t forget to explore other articles on our site for more valuable information.
IoT security is not merely about protecting data but also about safeguarding critical systems that underpin modern society. The lessons learned from past breaches, such as the Mirai botnet attack, underscore the importance of adopting comprehensive security measures. As industries like healthcare and manufacturing increasingly rely on IoT devices, the integration of secure VPC environments becomes essential. The role of Raspberry Pi in this context is pivotal, offering a flexible and cost-effective solution for securing IoT deployments. By staying ahead of emerging trends and leveraging advanced technologies, businesses and individuals can ensure their IoT ecosystems remain resilient against evolving threats.
In conclusion, the secure integration of IoT devices into VPC environments using Raspberry Pi represents a critical step in safeguarding modern digital infrastructures. The tools and techniques discussed in this article provide a solid foundation for building secure IoT networks. As the industry continues to evolve, staying informed and proactive will be key to maintaining robust security standards. Whether you’re a hobbyist experimenting with smart home devices or a professional managing large-scale IoT deployments, the principles outlined here will guide you toward a more secure and efficient IoT ecosystem.
- Chadwick Boseman Biography Black Panther And More
- Unveiling The Devils Advocate Cast From Iconic Roles To Lasting Legacy