In today's hyper-connected world, safeguarding IoT devices is no longer optional but a critical necessity. RemoteIoT firewall emerges as a pivotal tool designed to protect your network and devices against an ever-evolving array of cyber threats. For those eager to delve into the inner workings of this security powerhouse and learn how to harness its capabilities effectively, this guide serves as your definitive resource.
The exponential growth of Internet of Things (IoT) technology has brought about an unprecedented demand for robust security measures. RemoteIoT firewall offers a sophisticated solution, acting as a formidable barrier against unauthorized access and potential cyberattacks. This guide will take you through the entire spectrum of RemoteIoT firewall, from its foundational elements to advanced configuration techniques. By the conclusion of this tutorial, you will possess a comprehensive understanding of how to set up and optimize your RemoteIoT firewall for maximum security.
| Aspect | Details |
|---|---|
| Product Name | RemoteIoT Firewall |
| Release Date | 2022 |
| Manufacturer | RemoteIoT Technologies |
| Key Features | Real-time threat detection, customizable traffic rules, logging capabilities, multi-protocol support |
| Compatibility | Linux, Windows, macOS |
RemoteIoT firewall distinguishes itself as a cutting-edge security solution tailored explicitly for IoT devices and networks. It functions as a vigilant barrier, ensuring only authorized traffic permeates your system. Its versatility allows users to fine-tune settings to align with their unique security requirements. Whether you're an individual securing your smart home devices or a corporation protecting your expansive IoT infrastructure, RemoteIoT firewall is an indispensable asset.
- Angus Sampson Movies Wife Career Insights What You Need To Know
- Jodie Sweetin From Full House To Todays Tv Movies
IoT devices, increasingly targeted by cybercriminals due to their inherent security limitations, necessitate comprehensive protective measures. RemoteIoT firewall addresses this vulnerability by providing a robust security layer. Beyond safeguarding devices from unauthorized access and malicious attacks, it plays a pivotal role in preventing data breaches. These breaches can result in significant financial losses and tarnish reputations. By deploying RemoteIoT firewall, you can markedly mitigate the risk of data breaches, preserving the confidentiality and integrity of your information.
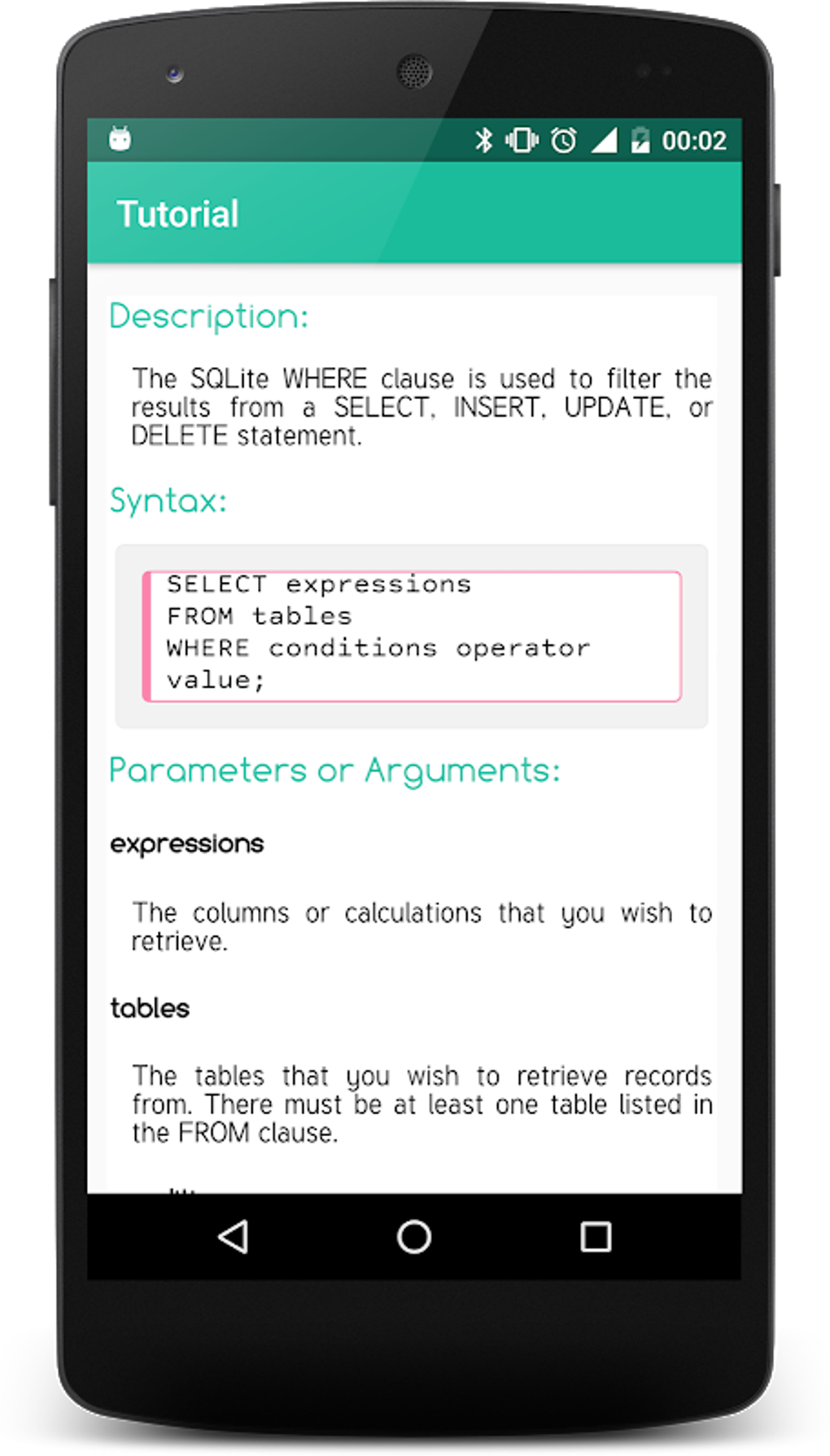
Compliance with stringent security standards is crucial across numerous industries. RemoteIoT firewall aids in meeting these obligations through advanced security features and comprehensive logging capabilities. Before proceeding with the installation process, it's imperative to grasp the foundational concepts underpinning RemoteIoT firewall. Understanding its architecture, key components, and interaction with your network will facilitate smoother implementation.
To guarantee optimal performance, ensure your system meets the specified requirements: a dual-core processor or better, a minimum of 4GB RAM, at least 20GB free storage space, and an operating system compatible with Linux, Windows, or macOS. The installation process of RemoteIoT firewall is relatively straightforward. Begin by downloading the latest version from the official website, then execute the installation package and adhere to the on-screen instructions. During installation, configure the basic settings, and subsequently verify the installation by checking the firewall's operational status.
- Lori Greiner From Earring Organizer To Shark Tank Icon
- Unveiling Benjamin Halls Resilience A Journey Beyond Limits
Post-installation, additional configuration may be required, such as establishing user accounts and defining access rules. Access rules dictate which traffic is permitted or blocked by the firewall. These rules can be crafted based on various criteria, including IP addresses, ports, and protocols. Configuring logging is equally vital, as it enables monitoring and analyzing network activity. Adjust the logging settings to capture the necessary information for security analysis.
RemoteIoT firewall incorporates advanced intrusion detection and prevention capabilities, detecting and blocking malicious activities in real-time. For enhanced security, integrate RemoteIoT firewall with a Virtual Private Network (VPN) to encrypt network traffic and shield your data from interception. Even with the finest security tools, challenges may arise. Common issues include connection problems, performance degradation, and log file errors. Solutions involve checking network settings, optimizing firewall rules, and ensuring adequate storage space.
Should difficulties persist, consult the RemoteIoT firewall documentation or reach out to their support team for assistance. To maintain optimal security, keep your RemoteIoT firewall software updated to access the latest security features and patches. Conduct regular audits of your firewall settings and logs to identify and rectify potential security vulnerabilities. Real-world applications of RemoteIoT firewall underscore its efficacy.
In one case study, a homeowner utilized RemoteIoT firewall to secure their smart home network, effectively shielding their devices from unauthorized access. Another case study highlights a manufacturing company's implementation of RemoteIoT firewall to safeguard their industrial IoT devices, ensuring seamless operations and data security. RemoteIoT firewall's importance in securing IoT devices and networks cannot be overstated. By following the outlined steps, you can proficiently implement and configure RemoteIoT firewall, enhancing your overall security posture.
IoT security is a rapidly evolving field, with RemoteIoT firewall standing at the forefront of innovation. As industries continue to embrace IoT technology, the need for robust security measures becomes increasingly apparent. RemoteIoT firewall not only addresses current security challenges but also anticipates future threats. Its adaptability and comprehensive feature set position it as a leader in the IoT security landscape.
In the context of global cybersecurity trends, RemoteIoT firewall aligns with efforts by major players such as Cisco and NIST. These organizations emphasize the importance of layered security strategies, which RemoteIoT firewall exemplifies through its multifaceted approach. By integrating RemoteIoT firewall into your security infrastructure, you contribute to the broader goal of building a safer digital world.
As the IoT ecosystem expands, so too does the potential for cyber threats. RemoteIoT firewall's role in mitigating these risks is crucial. It serves as a testament to the ingenuity and foresight of its developers, who have crafted a solution that meets the demands of today's interconnected environment. For those seeking to fortify their digital defenses, RemoteIoT firewall represents a significant advancement in IoT security.
In conclusion, the integration of RemoteIoT firewall into your security framework is an investment in the future of your IoT infrastructure. By embracing its capabilities and adhering to best practices, you ensure the resilience and security of your network. Share your experiences and insights in the comments below, and explore additional resources to deepen your understanding of IoT security. Together, let's champion a safer digital frontier.
- Anthony Kiedis Height Bio Chili Peppers Legacy All You Need To Know
- Justin Chambers From Greys Anatomy To Today A Look At His Life