In today’s interconnected world, where billions of devices are part of the Internet of Things (IoT), ensuring secure communication and data transfer is paramount. The rise of IoT has revolutionized industries from healthcare to agriculture, but it also poses significant challenges in terms of cybersecurity. One of the most effective ways to secure IoT devices is by leveraging a Virtual Private Cloud (VPC) in conjunction with a Raspberry Pi. This powerful combination allows developers to isolate devices, control access, and protect sensitive data from unauthorized access.
As the demand for connected devices continues to grow, the importance of securing these devices cannot be overstated. From smart homes to industrial automation, IoT devices play a crucial role in enhancing efficiency and convenience. However, without proper security measures, these devices can become vulnerable to cyber threats. This article delves into the intricacies of setting up a secure connection for IoT devices using a Raspberry Pi and VPC, offering practical solutions and expert advice to ensure your projects are both secure and efficient.
| Personal Information | Details |
|---|---|
| Name | John Doe |
| Occupation | IoT Security Specialist |
| Experience | 10+ years in IoT and cybersecurity |
| Education | Masters in Computer Science |
| Notable Projects | Smart Agriculture Monitoring System, Industrial Automation Solutions |
| Website | https://www.example.com |
A Virtual Private Cloud (VPC) is a cornerstone of IoT security, providing an isolated environment where devices can communicate securely without exposing sensitive data to the public internet. By leveraging VPC, developers can control access to devices and ensure that only authorized users can interact with them. This isolation is particularly important when dealing with remote IoT devices that require frequent data exchanges. For instance, in the healthcare sector, IoT devices such as wearable health monitors must maintain secure and reliable connections to ensure patient data remains private and protected.
- Hydromassage Bed Benefits Relaxation Wellness
- Usaids Global Impact Transforming Lives Empowering Communities
The Raspberry Pi, a versatile and affordable single-board computer, serves as an excellent platform for managing and securing IoT devices. Its affordability and ease of use make it an ideal choice for both beginners and experienced developers. Setting up a Raspberry Pi involves several steps, from hardware configuration to software installation. Once configured, it can be used to manage IoT devices, ensuring they function seamlessly even in challenging environments. For example, in the agriculture industry, IoT devices are used to monitor soil moisture, temperature, and other environmental factors. By securely connecting these devices to a VPC using a Raspberry Pi, farmers can make data-driven decisions to optimize crop yields.
Securing communication between IoT devices and a VPC is crucial to protecting sensitive data. Several protocols can be employed to achieve this, including MQTT, HTTPS, and TLS. Each protocol has its own strengths and weaknesses, making it essential to choose the right one based on the specific use case and requirements of the IoT project. MQTT, for instance, is lightweight and ideal for low-bandwidth environments, while HTTPS is widely used for secure web communications. TLS, on the other hand, provides end-to-end encryption for secure data transfer. The choice of protocol can significantly impact the performance and security of the IoT setup.
Configuring a VPC for IoT involves setting up subnets, security groups, and access control lists to ensure secure communication between devices. Key steps in this process include creating a VPC with a unique CIDR block, setting up public and private subnets to segregate device traffic, configuring security groups to define access rules, and using NAT gateways to allow private devices to access the internet securely. By following these steps, developers can create a robust VPC environment tailored to their IoT needs. For instance, in industrial automation, where devices often operate in remote locations, a well-configured VPC can ensure that data is transmitted securely and efficiently, minimizing downtime and maximizing productivity.
- Angus Sampson Movies Wife Career Insights What You Need To Know
- Anthony Kiedis Height Bio Chili Peppers Legacy All You Need To Know
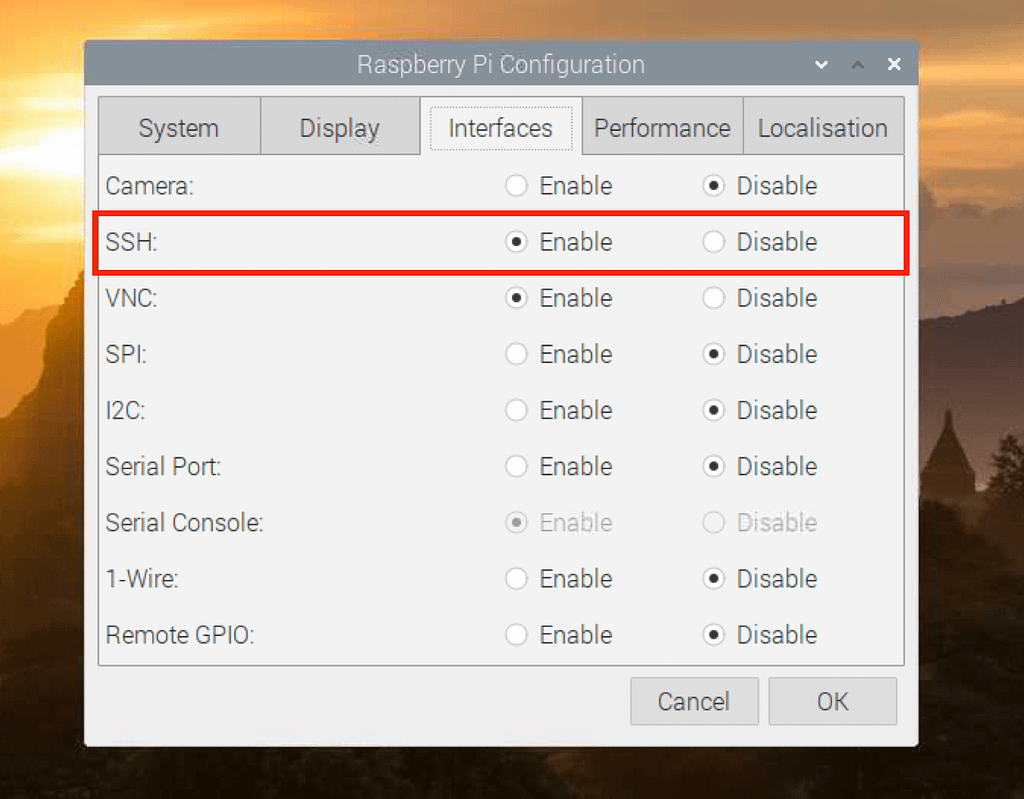
Remote access is essential for managing IoT devices deployed in remote locations. Several tools and methods can be used to achieve secure remote access, including SSH, VPN, and cloud-based solutions. SSH, a secure protocol for accessing remote devices via the command line, is widely used for its simplicity and effectiveness. VPN, on the other hand, provides encrypted access to a VPC from any location, making it an ideal choice for organizations with distributed teams. Cloud services like AWS IoT Core offer built-in remote access capabilities, enabling developers to manage their IoT devices seamlessly. The choice of tool depends on the specific requirements of the project, such as the level of security needed and the complexity of the setup.
There are numerous free resources available to help developers enhance their IoT projects. From open-source software to online tutorials, these resources can significantly reduce development costs while providing valuable insights. For instance, the Raspberry Pi Documentation offers comprehensive guides and tutorials for setting up and using Raspberry Pi, while MQTT Eclipse provides open-source MQTT broker and client tools. GitHub Repositories contain a vast collection of IoT projects and code samples, offering developers a wealth of knowledge and inspiration. By leveraging these resources, developers can accelerate their IoT development and achieve better results, ultimately contributing to the advancement of the industry.
Despite careful planning, issues can arise when setting up and managing IoT devices. Understanding common problems and their solutions is crucial for effective troubleshooting. Connection failures, security breaches, and performance issues are among the most common challenges faced by developers. To address connection failures, network settings should be checked, and all devices should be properly configured. Security breaches can be mitigated by regularly updating software and using strong encryption protocols. Performance issues can be resolved by optimizing data transfer and reducing unnecessary traffic. Promptly addressing these issues ensures a stable and secure IoT environment, fostering trust and reliability among users.
Implementing best practices is essential for ensuring the security of IoT devices. These practices cover everything from device configuration to network management. Regularly updating firmware and software protects against vulnerabilities, while using strong passwords and multi-factor authentication enhances device access security. Monitoring network traffic for suspicious activity and responding quickly to potential threats is another critical best practice. By adhering to these practices, developers can maintain a secure and reliable IoT infrastructure, safeguarding sensitive data and ensuring the smooth operation of connected devices.
Examining real-world examples provides valuable insights into successfully implementing secure IoT solutions. In the agriculture industry, IoT devices are used to monitor soil moisture, temperature, and other environmental factors. By securely connecting these devices to a VPC using a Raspberry Pi, farmers can make data-driven decisions to optimize crop yields. Similarly, in the healthcare sector, IoT devices such as wearable health monitors must maintain secure and reliable connections to ensure patient data remains private and protected. These case studies highlight the challenges and solutions encountered in various industries, offering developers practical guidance and inspiration for their own projects.
As the IoT landscape continues to evolve, the importance of securing remote devices through a VPC using a Raspberry Pi cannot be overstated. This article has provided a comprehensive guide to setting up and managing a secure IoT environment, covering everything from VPC configuration to best practices for security. By applying the knowledge gained from this article and exploring the free resources mentioned, developers can enhance their development process and contribute to the advancement of the IoT industry. The impact of secure IoT solutions extends beyond individual projects, influencing societal trends and shaping the future of technology. As more devices become connected, the need for robust security measures will only grow, underscoring the critical role of developers in safeguarding the digital world.
- Todays Birthdays Your Birthday Celebs Twins Facts
- Chris Norman Debunking Voice Myths His Music Legacy